| Dear , |
Cyber Security Newsletter May 2024 |
|
We are aware the newsletter below is quite lengthy and contains a lot of information to take in. However, we feel it is important for our customers to understand some of the risks and mitigation options. We encourage you to read the newsletter and ask us questions if you have any. This month we would like to address several Cyber Security items which could potentially have a great impact on your business. Additional to the information below we will also implement a couple of changes to most customer’s O365 tenant to mitigate some ongoing risks. These changes will have minimal or no impact to your day-to-day operations. Cyber Security is a responsibility of everyone who uses IT equipment including computers, phones, or networking equipment. In the current environment Hackers and Scammers (we will call them bad actors) are treating their objectives as a profession. They are highly skilled and quite often well organised individuals and even organisations who will spend a considerable amount of effort and time to try to steal from organisations and individuals. This is a recent case study: |
“Recently we had an end-user receiving an email from a known contact who asked him to open an encrypted document. As the known contact was a finance company, the request did not seem strange or out of the ordinary. However, the email from the finance company was compromised and the email received by the end-user was actually coming from a bad actor.
|
|
One of the most common threats we currently see is the attempt to intercept and change invoices so the recipient of the invoice will pay to a different bank account, one which is controlled by the bad actors. There are multiple ways this can occur. The recipient’s mailbox can be compromised and an email with an attached invoice can be downloaded, changed and re-uploaded so the recipient will have no indication anything untoward has happened and would possibly pay the invoice to the fake bank details inserted by the bad actors. Another option is that the sender’s mailbox could be compromised, and the bad actors could insert themselves into an existing email correspondence. This will install trust into the recipient and any information given by the bad actor has a high probability of being treated as real. The difficult message IT companies have to relay to their customers is that no amount of technical measures can stop all instances of potential compromises of emails or data. The most common threat is deception of end-users by making them believe they are speaking to a known contact or organisation while they are dealing with a bad actor. Just a couple of examples of these are:
As these bad actors are highly skilled in pretending to be someone or something they are not, it can be very difficult to distinguish between a real of a fake communication. This kind of hacking is known as ‘Social Engineering’. Regardless of what technical measures we’ve put in place to make your environment safer, if bad actors succeed in persuading an end user to, even unknowingly, handing over the keys to the kingdom, then the amount of damage they can do is considerable. There is a mixture of measurements we recommend to mitigate these issues, but none of them will give you a guaranteed outcome.
The cyber security landscape is constantly evolving, and the length of this newsletter does not allow us to talk about all options or threats. We have tried to identify and address some more common risks and protection options. That does not mean that other options should not be considered or are less important. We are always happy to book a time to have a more personalised chat with you about measures available to your business. Please book a meeting with Iwan and/or Tony if you would like to discuss Cyber Security in more detail or if you have any further questions. Just for reference, this link is to an article by Microsoft explaining how Social Engineering can work: |
 |
|
Some other interesting links: https://www.knowbe4.com/what-is-social-engineering https://ia.acs.org.au/article/2023/car-buying-couple-loses--139k-to-invoice-scam.htm Nine ways MFA can be breached (and why passwords still matter) - Specops Software Ransomware gang targets Windows admins via PuTTy, WinSCP malvertising (bleepingcomputer.com) |
Highlighting Oscar (Again): |
 |
!! Oscar is now the ABit Systems Support Manager !! |
|
Oscar started with ABit in January 2023. After arriving in Australia from Colombia to learn English he met Tony and Leah by chance on a Transperth service. He told Tony and Leah that, in Colombia, he worked in technology, and they asked him to send in his resume. He writes “a vacancy opened quickly and after a couple of interviews I started in what I call a miracle from God. ABit gave me the opportunity to work while learning English which was a miracle for me.” On a personal level Oscar writes: “My favourite topic is definitely technology, especially cybersecurity, I am also very interested in music, 2 years ago I started learning to play acoustic guitar and I practice at least 2 times a week. I also like to read, especially Stephen King's books. Likewise, I attend church every day to be in communion with God. Oscar always has a smile on his face! |
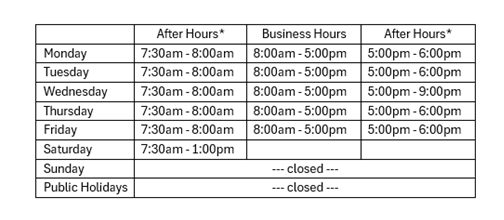
After Hours support |
 |
| Currently ABit has the following hours of operation: |
 |
|
*After Hours support attracts the After Hours Hourly rate and is out of scope of any MSP contract. We are interested in feedback on our opening hours, please send any suggestions to our General Manager. |

